Win32 Find GetProcAddress
Overview
Goal
Find the address for the symbol(function) GetProcAddress, within kernel32.dll.
GetProcAddresscan then be used to retrieve the adress of other symbols within Dynamically Linked Libraries (DLL’s).
Requirement to Finding GetProcAddress
First you must find the base address of kernel32.dll.
- Reference my previous post to understand this.
Technique
Export Directory Table
- As detailed in Skapes Windows 32 Shellcoding paper
Tools
- PEview
- OllyDbg
- Windows Vista Home SP1 x86
- nasm (kali)
- Immunity Debugger
Steps to Finding GetProcAddress
- Get the base address of
kernel32.dll - Find offset to New EXE Header within the
Image_dos_Headerofkernel32.dll(BaseAddr of kernel32.dll) + 0x3c = (PTR to New Exe Header)- This RVA holds a pointer to 0xe0 (RVA of New Exe Header)
- For windows Vista SP1

- Find Offset for the Export Table within
Image_optional_header(RVA of New Exe Header) + 0x78 = (PTR to RVA of Export table) 0xe0 + 0x78 = 0x158- This RVA holds a pointer to 0x00C009C
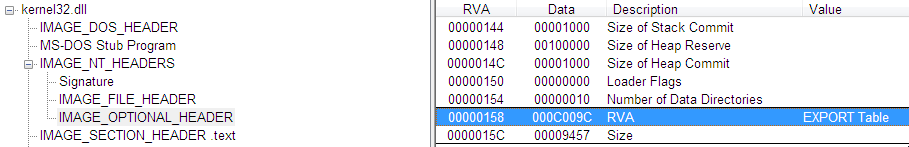
- This RVA holds a pointer to 0x00C009C
- Find Offsets for Address Table, Name Pointer Table and Ordinal Table from Export Table
(Addr of Export Table) + 0x14 = Number of Functions/Symbols within the Tables (Addr of Export Table) + 0x1c = (PTR to RVA of Address Table) (Addr of Export Table) + 0x20 = (PTR to RVA of Name Pointer Table) (Addr of Export Table) + 0x24 = (PTR to RVA of Ordinal Table)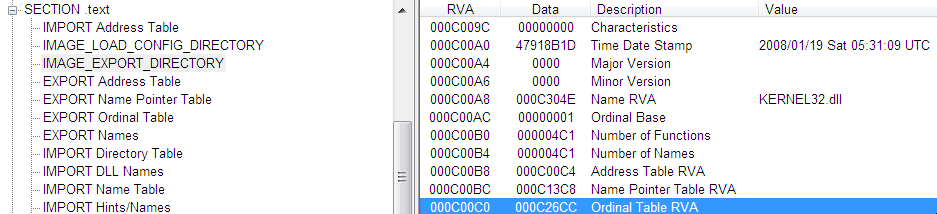
- Loop through Name Pointer Table comparing each string with “GetProcAddress”
- Make sure to keep count of placement
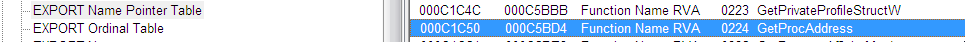
- Make sure to keep count of placement
- Find GetProcAddress Ordinal number from Ordinal Table
(Addr Ordinal Table) + (Position "GetProcAddress") * 2 = GetProcAddress Ordinal #- Each entry in the Ordinal Table is 2 bytes.

- Each entry in the Ordinal Table is 2 bytes.
- Find GetProcAddress RVA from the Address Table
Addr of Address Table) + (Ordinal Number) * 4 = RVA GetProcAddress - Get full address of GetProcAddress
(kernel32.dll base-addr) + (GetProcAddress RVA) = Full-Address GetProcAddress
References
http://sh3llc0d3r.com/windows-reverse-shell-shellcode-i/https://0xdarkvortex.dev/index.php/2019/04/01/windows-shellcoding-x86-calling-functions-in-kernel32-dll-part-2/https://idafchev.github.io/exploit/2017/09/26/writing_windows_shellcode.htmlhttp://www.hick.org/code/skape/papers/win32-shellcode.pdfhttps://www.corelan.be/index.php/




